Information Security
I. Framework:
- The "Information Security Committee" was established to promote, coordinate and supervise information security operation. The updated status shall be reported to board of directors at least once a year. In addition, the company has obtained international information security certification to reduce security risk and protect customer privacy.
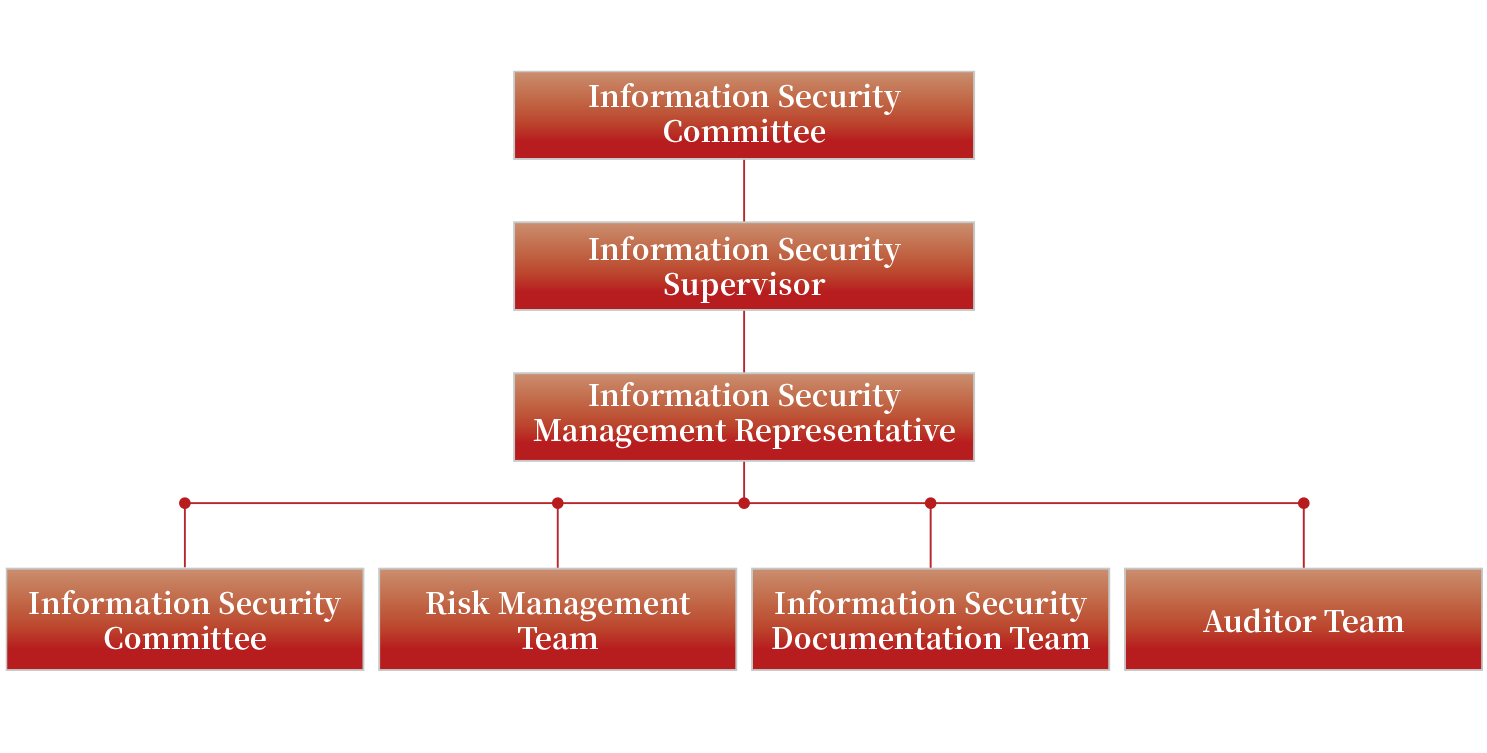
II. Policy:
- Purpose: Strengthen security management, ensure confidentiality, integrity and availability of the relative information to build up a sustainable information environment for sales operation; while comply with government regulation and external/ internal stakeholders ’requirements to avoid any intentional or accidental threats at the same time.
- Target:
- Ensure the correctness, completion and practicality of the company’s information.
- Ensure the confidentiality of the company's important information and implementation of data access control. Information access or storage shall only be conducted with the approval of authorized personnel.
- Ensure the compliance with legal regulations.
III.Plan:
In order to enhance information security management, the company has completed the re-assessment, extended validation, and transition to ISO 27001:2022 "International Standard for Information Security Management System" in 2025. The certificate is valid from August 11, 2025 to August 10, 2028. The standard-based mode and guideline were executed and implemented into daily operation to further improve security protection. The company has set concrete management plans as follows:
- The company regularly conducts propaganda and promotes the importance of information security. New employees must participate in educational training to enhance the awareness of information security protection.
- Build up a safe and reliable information environment to enable sustainable operation.
- Appropriate backup or monitoring mechanisms should be established for important information systems or equipment. Regular drills should also be conducted to assure availability.
- Anti-virus software should be installed in every employee’s computer and virus code should be checked regularly. Unauthorized software is prohibited.
- Accounts, passwords, and authorizations held by individual should be fully maintained and replaced periodically.
- Design appropriate response and notification procedures to respond immediately to information security incidents.
- The company has conducted information security risk assessment and audits every year to ensure the effectiveness of management and compliance with regulations. Risk of information security is not a major issue and there is no need for insurance currently.


